The National Motor Freight Traffic Association last year issued an advisory to carriers with in-truck systems connected to outside networks, whether the internet, the cellular network or satellite tracking. The bulletin noted “there are a number of steps to take to reduce the risk” of a security breach.
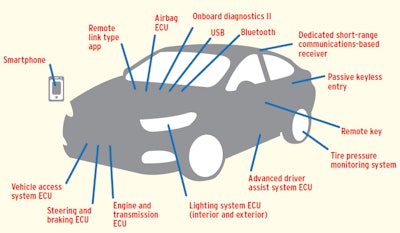 POTENTIAL HACKING GATEWAYS. This diagram, presented at a NAFA Fleet Management Association’s 2016 meeting, illustrates the variety of automobile entry points that present opportunities to malicious programmers. The federal requirement to use an ELD will add a potential entry point to thousands of heavy-duty trucks at yearend.
POTENTIAL HACKING GATEWAYS. This diagram, presented at a NAFA Fleet Management Association’s 2016 meeting, illustrates the variety of automobile entry points that present opportunities to malicious programmers. The federal requirement to use an ELD will add a potential entry point to thousands of heavy-duty trucks at yearend.Anyone plugging a device into the onboard diagnostics port, particularly an ELD that will open up a connection between the truck’s computer and the internet, would do well to:
-
- Make certain vendors take security seriously. This should include having a security team in place to push out timely security updates to the device to prevent malware and guard against other infiltration.
- Disable or remove features that enable remote access to a third party, such as remote diagnostics services, if you’re not using them.
- Maintain consistent communication with vendors, including providers of ELDs/telematics, “to ensure that you are notified of any critical security issues or updates to your equipment and service.”
- Check regularly for updates, whether your device is internet-connected or communicates locally only. Include updates to system software within 30 days of release, including those from truck manufacturers.
- Make cybersecurity protocols a standard part of your pre-trip inspections to catch any physical threat, such as from “foreign devices mounted to accessible parts of the vehicle that can connect to the” engine’s computer – “an easy way to prevent onboard access” from an unknown party, perhaps the biggest threat today for owner-operators.
- Be cautious about modifying the engine’s computer. About third-party devices, “make sure that any modifications or additions to your vehicle … do not compromise the security of your vehicle or bridge networks which have been separated” by the manufacturer.