The University of Michigan made news last year when researchers presented at an August conference results from their experiments with the vulnerability of big rigs’ electronic systems. As reported in Wired magazine ahead of the conference, researchers plugged into a 2006 tractor’s OBD II port, and this was in part the result:
By sending digital signals within the internal network of a big rig truck, the researchers were able to do everything from change the readout of the truck’s instrument panel, trigger unintended acceleration, or to even disable one form of the semi-trailer’s brakes. And the researchers found that developing those attacks was actually easier than with consumer cars, thanks to a common communication standard in the internal networks of most industrial vehicles, from cement mixers to tractor trailers to school buses.
In the months following the report, there have been a variety of discussions of the issues ranging from a webinar reported on by Tom Quimby at Overdrive sister site HardWorkingTrucks.com to excerpts from a TED talk by Avi Rubin about vulnerabilities in all manner of “smart” devices that was broadcast on the Ted Radio Hour show on National Public Radio a couple weekends ago.
Rubin’s talk centered around the growing IoT (“Internet of Things”), with not only connected phones and traditional computers but home appliances, personal autos and the like.
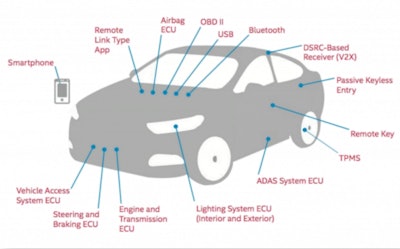 This slide from the NAFA Fleet Management Association’s October presentation on and discussion of vehicle hacking risk illustrated the variety of entry points that presented opportunity for malicious programmers. Read more about the discussion’s assessments of risk and ways to combat it via this link.
This slide from the NAFA Fleet Management Association’s October presentation on and discussion of vehicle hacking risk illustrated the variety of entry points that presented opportunity for malicious programmers. Read more about the discussion’s assessments of risk and ways to combat it via this link.A lot of new equipment now comes Internet-connected or at least capable of being connected, of course, and with the electronic logging device mandate set to take effect later this year, the IoT might well become an appropriate acronym for an “Internet of Trucks” in a much bigger way – all but one ELD listed on Overdrive’s quick-comparison chart (the Continental VDO RoadLog is the exception) of the steadily proliferating available e-log systems on the market come with a monthly service plan, most often associated with a connection to the cellular data network. Those systems are in large part connected to the engine via the OBD port and set up to receive data directly from the engine’s electronic control module in 2000 and newer model year trucks, most of the fleet on the road today.
That connection presents vulnerabilities to those with malicious intent that designers of the systems increasingly are having to consider. “I think we’re at an inflection point in the industry,” says Sharon Reynolds, Omnitracs’ chief information security officer, beyond which guarding against vulnerabilities should be even more of a chief concern for everyone operating within it. “It’s critical that we continue to mitigate those risks. I expect and welcome dialogue to continue throughout the industry. We all have a hand in this game” of guarding against the possibility of a third party taking control of the truck in the manner of the University of Michigan researchers referenced above – or in any manner as yet unforeseen.
Portland, Ore.-based owner-operator Chris Guenther, at least, knows what it feels like to lose some of his control.
Last summer, he was fresh out of the shop where he’s had $9,000 worth of work put into the emissions system in his 2012 Kenworth T700, powered by a Cummins ISX. The work was prompted by a variety of fault codes from his ECM. Going across Southern Ohio toward Erie, Pa., on a secondary route “trying to avoid tolls … in the middle of nowhere,” he says, his Omnitracs MCP50 on-board unit started to act up. “Like the old tube PCs with lines up and down in the screen – it started doing that, then started moving me from driving to off-duty to driving or on duty not driving” for no apparent reason. “Shortly after that, my dashboard started popping all kinds of engine and re-gen codes. The truck then de-rated” slightly with the fault codes, but Guenther was many miles away from a good place to pull off or get service. “Where I was I had no shoulder. The white line was the edge of the road.”
He continued as quickly as he could with the de-rating of the engine – less than 60 mph – and called the shop that had just worked on the truck. The mechanic there told him to contact Omnitracs directly. “I explained to [Omnitracs] what was going on and what was going on with my truck – that I’d had those parts replaced recently – and they said they could do a forced reboot.”
Keep in mind, Guenther is still moving down the road, talking to the rep on the phone. “He told me, ‘It’s going to shut down and reboot five times in a row,’” with about 10 seconds between each reboot. “So he does that, and when the MCP50 shut down, so did my engine. It did that five times. And when it shut down my engine, I’ve got nothing. The power-steering is gone, the air brakes… . Finally, the last time all my engine codes were gone.”
The rep, told what was happening: “This doesn’t normally happen.”
Talking with Omnitracs executives, “we don’t have another documented case like this,” said Scott Hildebrand, vice president of support and customer experience, who reviewed Guenther’s call and data from his unit on the day in question. “When we looked at the data from the unit we had available – we definitely see the unit reset and see the unit come back up, but we can’t prove or disprove anything that happened out there.”
Guenther adds that water could have been at play to one degree or another, noting a concurrent problem with moisture and the electrical system. “I’ve got an issue with water getting into my harness plug [on occasion] that kicks off a slew of different codes.”
Asked about Guenther’s case, Cory Hunt of Pivot Technology Resources notes he’s heard of some similar cases in his years working with on-board electronics from Omnitracs and others. “When you’re tying into the data connectors and some of the wiring in these trucks,” he says, “they’re all integrated into the functionality of the trucks themselves. I’ve seen it where the on-board unit won’t even let the truck shut off.” I.E. you turn the ignition off and “take the key out,” but the truck won’t power down without powering down the on-board communications device.
“It could be a matter of crossing up a couple different wires. It could be a resistor on a board in the wrong spot. I’ve seen some really crazy things over the last 17 years. They’re funny to hear, but yeah in that position and you have something like that happen,” they can also be scary, he adds.
Fortunately, such instances are “very rare,” Hunt says. “I could count on one hand the number of times [he’s heard of] something like that happening in the 100,000s of units” that have been moved over his career.
 Have you experienced a similar electronics-related issue? If you’re reading on a smartphone, tap the image to call and leave us a message to weigh in with your story. We’ll round up responses in a special mailbag podcast. Alternately, drop a comment below. If you’re on a desktop, call 530-408-6423. Make sure to tell us your name and state of residence.
Have you experienced a similar electronics-related issue? If you’re reading on a smartphone, tap the image to call and leave us a message to weigh in with your story. We’ll round up responses in a special mailbag podcast. Alternately, drop a comment below. If you’re on a desktop, call 530-408-6423. Make sure to tell us your name and state of residence.But happen they have, suggesting that if you have the potential for malfunction in the electronic system governing your truck, ensuring the integrity of it will be doubly important when plugging in any IoT device, including an ELD.
Regarding security of the ELD system from outside would-be infiltrators, says Omnitracs’ Reynolds, “When you select the IoT device, make sure it was engineered with security in mind.” A company like Omnitracs has a “large security staff,” she adds, likewise the capability of over-the-air software updates, enabling quick protection against potential malware infecting the device and causing further malfunctions.
In Guenther’s case, he says, his customer-support rep during the incident described above speculated an over-the-air update didn’t go through to his unit because of a solar storm happening at the time the update was going through, possibly contributing to the issues he experienced. Though his unit had run OK for months following this particular incident when we talked, it has since malfunctioned in similarly odd, unprompted ways, shifting his duty status without input — to the point that he’s keep paper logs in addition to running the ELD as a constant back-up.
And at once, his mind continues to run over the questions raised by the whole scenario. If the Omnitracs rep can obviously control the unit from afar, who else might be able to? He takes that further, noting that if fault codes are being thrown by the ECM, “What’s to say that’s not somebody hacking the system” via the cellular networks “and telling it that something’s wrong. It scares the hell of me – a huge Pandora’s Box.”
To date, there’s no evidence out there that a truck has in fact been maliciously hacked, just as it was six years ago when I first wrote about the possible eventuality. And the University of Michigan researchers were operating plugged into the truck, i.e. far from simulating what would likely be a more difficult, remote-access hack of truck systems.
But, says Omnitracs’ Reynolds, the questions Guenther’s asking are the right ones. “I think it’s important for all of us to ask those questions,” she says, and work together – telematics providers, OEMs, customers and industry advocates all – to continue to prevent potential attacks.
The National Motor Freight Traffic Association, Reynolds notes, issued an advisory to carriers in September with in-truck systems connected to outside networks in mind, whether the internet generally or the back office via the cellular network or satellite tracking.
The bulletin noted that, “while short-term solutions to vehicle computer designs are limited, there are a number of steps to take to reduce the risks.” Maintain consistent communication with vendors, including providers of ELDs/telematics, “to ensure that you are notified of any critical security issues or updates to your equipment and service.”
If your truck is connected to the Internet, make certain vendors have a security team in place to make and push out timely security updates to the device or to the truck. If your device communicates locally only – not connected to the Internet via the cellular network or otherwise – check regularly for updates yourself. Include updates to system software within 30 days of release, including from vehicle manufacturers themselves.
About third-party devices, the report notes it’s critical to “make sure that any modifications or additions to your vehicle … do not compromise the security of your vehicle or bridge networks which have been separated by the OEM.” Also reduce the potential points of attack by disabling or removing “unused features that are not critical to the use and functionality of the vehicle, especially those that enable remote access.”
Make cybersecurity protocols a standard part of your pre-trip inspections to catch any potential threat, such as from “foreign devices mounted to accessible parts of the vehicle that can connect to the” main controller area network bus – “an easy way to prevent onboard access” from an unknown party, perhaps the biggest threat today.
Those interested can download the full NMFTA security bulletin at this link.