Multiple brokers on Monday showed signs of falling victim to a hack that saw hundreds of load postings flying onto DAT's load board quicker than the users could delete them, and perhaps even defeating DAT's own revamped security measures.
"It was on Monday," said Tina Giramma, a broker at ST Freight. "I had gotten a couple emails about some random load that's not my load. It happens every now and then." Yet when she "opened up DAT, the whole damn page was full of postings. I kept scrolling and went, 'oh crap,'" before letting the enterprise account holder know someone had gotten into her account.
Giramma is the only user on her account. Yet somehow, other users were simultaneously logged in with a different IP address and posting loads.
"I couldn’t delete them fast enough," she said. "As soon as I would delete 150" loads, "150 more would pop up."
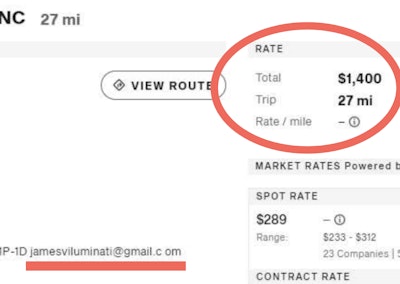
Now Giramma had carriers emailing her about the loads, and some of the postings' more eye-popping details emerged. $1,200 for a 27-mile haul from Charlotte, North Carolina, to nearby Concord, power only, dropping off in a Circle K parking lot. A similar set popped up near Amazon's Kent, Washington, distribution centers.
Does that sound fishy to you?
[Related: Chicago-area freight thief steals $9.5M in goods: Courts]
"Everything on the posting showed correctly as an ST Freight load, except for the note in the commodity section that says the email," said Tony Abts, ST general manager. "The email that they put in there is [email protected] om. Notice the space in the word c om."
Other postings from ST and other brokers had another email address listed, also with the space, but a few did not. In total, likely a few thousand went up across a few brokers.
This scammer's or scammers' mission, Abts observed, was to "bulk download hundreds of power only loads. From what I could tell, these are trailer moves from Amazon facilities."
Further research revealed two IP addresses accessing ST's accounts in particular. One VPN address basically presents as untraceable. The other seemed to lead back to Amazon's Boardman, Oregon, data center, said Giramma.
"Possibly an inside job" involving someone with knowledge of Amazon's logistics operations, Abts speculated.
Overdrive won't pretend to know how Amazon's data centers work, but Amazon's web services do, generally, hold up a large part of the internet's infrastructure. Of course, the scammer might just be "spoofing" an IP address to throw off would-be investigators.
Overdrive reached out to Amazon and reported these findings, but did not hear back.
Inside job or not, the hacker here seemed intent to move trailers from an Amazon warehouse to a nearby location -- that Circle K parking lot in ST Freight's case, where they might easily be stolen. Despite efforts of carriers, brokers, load boards like DAT and Truckstop and so many others, cargo theft has soared in recent years, up 10% last quarter, 46% year over year, while freight fraud jumped 130% in 2023.
As Giramma frantically deleted the postings coming from the ST Freight accounts, messages from carriers poured in, some identifying the obvious scam and confronting her about it, others just inquiring about the quite profitable load.
"I kept trying to delete as fast as I can, thinking DAT is going to get me shut off immediately," said Giramma. "There should be an option where you can disable your account immediately."
Instead, she said it took an hour and a half for DAT to step in.
Giramma uses two-factor authentication, a tool that's supposed to help keep unauthorized people out of her account, heralded as a big security achievement within the last year by both DAT and Truckstop load board networks.
[Related: Inside the fight against 'cyber crime' in brokered-freight networks]
"DAT’s other big thing was whatever email address is on the account, you’re not supposed to be going into the commodity [field on the posting] and putting an alternate email address in there," she said.
In 2023 DAT announced that it "disallowed non-profile contact information in the shipment free-text fields."
But Giramma was staring in the face hundreds of postings with the non-profile contact information, not just from her brokerage, but from others, including Landstar's.
Overdrive asked DAT about the hack, and a PR firm hired by DAT strongly implied the brokers had made mistakes allowing their credentials to be compromised. DAT wouldn't comment officially, but the firm did address some of the specifics of the hack. "Generally speaking, scammers use spaces and special characters to circumvent filters that prevent email addresses in comment boxes," they said. "Developers make better filters, scammers adapt, users get fooled, and the cycle starts all over. It’s a race with no finish line."
That's exactly what happened on hundreds of the phony loads posted under legitimate broker accounts. A simple space bar keystroke seemed to have defeated a piece of DAT's security regime.
Overdrive contacted another broker whose account got hacked, and they said that DAT informed them they had fallen for a phishing email.
"We got an email from [email protected] saying that we got a bad review on DAT, and I saw in that box it's some carrier I've never worked with," the broker said. But that email address is fake, and the link it contained to sort out the supposed errant review led the broker to enter their login credentials, giving the scammer full access despite the two-factor authentication.
Giramma had the same email in her inbox several times, but said she had never clicked the link and is very careful with phishing and carrier selection. "First off, I am a big anti-double broker," she said. "I am like the carrier nazi" she joked, rejecting carriers with any whiff of suspicious or incomplete information.
"It angers me to the point where I hate it, it’s scary," she said of the volume of freight fraud in the system right now.
[Related: 'Fake safety audit' phishing emails keep pouring in: How to spot the scam]
For Giramma, the entire episode raises more questions than just a simple hack or attempt at cargo theft. Did the scammer succeed in getting a truck to move any of these loads? Did the load get stolen? Was the truck driver paid in the deal?
What happens if some foolhardy carrier books the load, hauls it, and then reaches out to ST for payment? "It's a mess when it does happen," she said.
To keep from damaging shipper relations, her brokerage "might have to come out of pocket" when a load gets double brokered, she said.
Giramma has almost two decades of experience in freight and knows backwards and forwards the best practices for avoiding fraud, but she said it's still a constant struggle. "You can vet a carrier all day long and everything can look great and wonderful and bam! Bob decided he was done with the business and Jimmy came and gave him $1,000 to use his MC number," and now that vetted carrier represents another security risk.
[Related: How do you know you're working with a double broker? Increasingly, it's hard to tell]
Furthermore, what happens when the market turns around? When Giramma can't be so picky with carriers?
Overall, Giramma said her experience over the years using DAT's load boards has left her suspicious of the company. "At my old job, we only posted our loads on DAT and we'd always look in the DAT directory for any reviews when we'd get a carrier," she said. "But so many of them weren’t in the DAT directory, it drove me crazy. Why am I getting emails and phone calls not even registered with DAT, and this is the only place my load is on?"
The answer, she felt, was "an office full of scammers under one DAT account just adding additional users and those users use other MCs."
DAT account holders pay about $50 to $200 depending on the plan for additional users, she said. Giramma suspected that DAT just liked selling additional users, and didn't want to crack down on the problem because it might hurt sales.
So much mystery surrounds the hack. "I emailed him and told him I like his name, James Iluminati," she said.
Giramma got in touch with other hacked brokers posting the loads, spreading awareness about the potential danger. Luckily, she heard from a lot of carriers who accurately recognized the fraud and didn't email the supposed Mr. Iluminati. Rather, they found the correct ST Freight contact and emailed her directly.
Let it be a reminder that such dangers are present -- if a load is paying $20/mile, that might be one of those too-good-to-be-true situations worth double checking.
[Related: Norman Camamile's weekend with the 'Iluminati' hacker: Four Amazon loads, no payment]