National Motor Freight Traffic Association Cybersecurity Director Artie Crawford has seen it firsthand. Even the most ostensibly cyber-aware of individuals can fall victim to the tricks of the hackers' trade in today's world of what's known as "social engineering." That is, efforts via email (phishing), text message (smishing) and voicemail (vishing) to trick you into giving up something you fundamentally don't want to give up. Information, sure, but ultimately these infiltrations are going after what any successful business owner wants, too: Your money.
Regular Overdrive readers are pretty aware that crooks just get more and more creative in their tactics -- even successfully impersonating federal safety auditors in memorable cases within the last year. Yet there's plenty individual owner-operators can do to help themselves play defense, starting with what Crawford and NMFTA Principal Cybersecurity Engineer Ben Wilkens call "personal cyber hygiene."
Crawford and Wilkens presented ways to build that basic defense Wednesday, September 10, with the first in a three-part weekly series with the Owner-Operator Independent Drivers Association dubbed "Cybersecurity Basics for Owner-Operators." The next session in the series takes place September 17, 5-7 p.m. Central, the final third following a week later at the same time September 24. There's a cost to register, and all three parts of the series will be available to registrants on-demand anytime they register, whether they're able to catch the live session or not, Crawford said.
The registration page is accessible via this link.
Key takeaways from the fist session?
Stakes can be quite high
Social engineering-enabled hacks and thefts could come in the form of tricking you into giving up your bank account password, whether or not it's a good one. Crooks might then drain the funds, of course, or perpetuate more-involved takeovers and demands for ransom payments that Crawford notes increasingly are tailored to the crooks' perception of the victim's willingness/ability to pay.
In the trucking business, "cyber criminals do not just target the big carriers," Crawford said, contrary to popular myth. "They’re out for the target they can hit the quickest and the fastest, and make the most money" from. That is, he added, the "most money you’re willing to part with."
While a huge trucking company may have a couple million sitting around for a ransom, "what cybercriminals are good at is targeting a number that will hurt you but that you're willing to pay," he said.
In some cases, it means loss of the business entirely. Crawford shared the example of a small fleet auto hauler who fell victim to theft of a full load of high-end autos, the theft itself enabled by social engineering online. The aftermath of the incident had all parties in the move scrambling, the carrier filing a cargo claim and having to pay the deductible for the insurance. Little did the business know, though, that it'd "paid the bad guy the deductible," too, Crawford said, so it lost that money along with all of the cars. "And here’s a carrier that has to close up shop. By sending them the money they gave access to their bank account."
[Related: Beware of double brokers: Getting involved with one can be a huge knock on business credibility]
It's a worst-case scenario for outcomes Crawford's seen in his time at NMFTA, he noted. Guarding against the worst happening is a matter of getting those passwords up and beyond 8-14 characters, and otherwise using multi-factor (sometimes called two-step) authentication (MFA) when it's available, helping secure all of your online accounts both personal and business-related.
Likewise: Security of the devices and software you use to access them. Use screen locks, with PIN logins required to unlock, for physical security of any device you might accidentally lose or otherwise leave unattended in a public place like a truck stop.
Keep on top of implementing the device manufacturer's updates, increasingly simple with automated procedures for most mobile devices -- laptops, too, in many cases. Yet be aware of end dates for security-update support. Depending on the manufacturer, that end date could be sooner than you think.
"Eventually every operating system, every device, it reaches end of life and it no longer gets updates," said Wilkens. "You can go to pretty much any manufacturer and you can look up their end-of-life dates. ... That's really one of those things you want to be planning for."
Keeping current software updates for the browsers you're using, too, will help when it comes to those individual browsers' security. That can go for any app on the phone as well, and don't be shy about researching any app you're considering downloading to reinforce your confidence in it and/or whatever service/entertainment/utility it provides.
"Apps have to publish the level of information they're collecting," said Wilkens. If it's beyond your comfort level or must access the camera, microphone or location services, weigh the cost-benefit of whether you really need to download that app or not.
Wilkens advised, too, to check security information in the Apple app store or Google Play, where you can see whether your device's operating system is compatible with it for security.
Both Crawford and Wilkens offered a great deal of detail around being wary of what you're downloading or opening from attachments (be extremely wary of .exe executable files), spotting questionable websites and more in the session. Crawford distilled a few additional, virtually no-cost "personal cyber hygiene" action items in the aftermath, some of them finer points of using device settings to protect yourself. Some are sure to come up in more detail in the next session September 17, "Cybersecurity on the road":
- Turn location services off on your mobile devices when they're not needed.
- Restrict apps when not in use.
- Remove permissions from apps when they are not needed -- including access to the microphone, camera and location services.
"We discuss open Wi-Fi and the use of VPNs, what they are and what they aren't, to ensure that folks understand that VPNs are not a failsafe," Crawford said. "They are just a tunnel that provides a secure-ish channel to and from a site. If the site is bad, it's still a bad site."
[Related: Norman Camamile's weekend with the 'Iluminati' hacker: Four Amazon loads, no payment]
Recognize 'social engineering' red flags
Notwithstanding refreshers on all of that "cyber hygiene," if you can effectively do this, you're like as not to avoid some of the biggest hits possible.
Often, the most effective scams come with a sense of urgency targeted specifically to you. The scammers have done their research about you, combing information you've shared online or that's available about the business in federal or state filings. They then hit you with something designed to really get your attention.
Crawford shared the example of a friend among his close colleagues going back decades in the military in cybersecurity. The colleague over the years became the Chief Information Security Officer for a Fortune 25 company -- theoretically at the top his security game, as it were. The friend's sitting in his office with two of his division heads conducting the morning cybersecurity meeting when he gets an email from his daughter's school:
Dear Mr. Jones, We see Elizabeth is in fear of not making the number of total days required to complete the semester. She's only allowed one more absence before she'll have to do remedial classes and possibly not be elevated to be a high school senior next year.
Follow this link to access your daughter's attendance record.
Urgent, to say the least -- he puts in a quick call to his wife, who tells him Elizabeth has been a model student and has perfect attendance. Yet he doesn't believe it, asking her to call their daughter on his cell phone to make certain his daughter is actually in school today.
He gets on the phone with the school's main office as his colleagues look on. The school tells him the same thing, despite what he sees when he clicks that link, his browser likely also downloading malicious software in the process.
His colleagues then chuckle nervously on their way out of the room as he realizes he's fallen for social engineering just like the untold thousands of others out there who've been effectively separated from their personal information -- and cash -- this way.
Yeah, it can happen to anyone, even the Chief Information Security Officer. No one is "immune to this" kind of manipulation, said Crawford. Be on guard for urgency of this type in any unsolicited communication, particularly when it's accompanied by links and/or documents or other files to download.
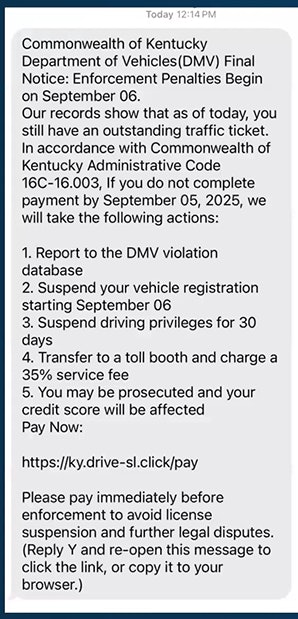 Likely you've seen an example of this one in your texts of late, projecting that urgency, authority and solicitation social-engineer-type scammers increasingly use to good (for them) effect. (And as you probably guessed, "Kentucky Administrative Code 16C-16.003" doesn't exist, which a quick Google Search would tell you.)
Likely you've seen an example of this one in your texts of late, projecting that urgency, authority and solicitation social-engineer-type scammers increasingly use to good (for them) effect. (And as you probably guessed, "Kentucky Administrative Code 16C-16.003" doesn't exist, which a quick Google Search would tell you.)
"Stop. Take your time," he said. "Examine the facts. Ask someone, ask a trusted party" for advice as to, for example, whether it's your bank or "somebody pretending to be your bank" or the DMV actually contacting you with an urgent request. Then: "Decide on what's the safest response. And quite often it's going to be to ignore the message. Delete the message. Hang up on the phone."
Ultimately, "You're in charge," he said. "I'm very passionate about this because I see people get hoodwinked by these scam artists all the time."
[Related: With ID theft on the rise with other scamming, guarding your business is a necessity]










