The University of Michigan made news in August 2016 when researchers at a conference presented results from their experiments with the vulnerability of big rigs’ electronic systems. As reported in Wired magazine ahead of the conference, researchers plugged into a 2006 tractor’s OBD II port and largely commandeered the truck’s internal network. In this hack simulation, researchers “were able to do everything from change the readout of the truck’s instrument panel, trigger unintended acceleration, or to even disable one form of the semi-trailer’s brakes.”
The experiment followed previous high-profile researcher hacks of consumer vehicles, exploiting vulnerabilities in the cars’ over-the-air-connected infotainment systems. Researchers were able to disable acceleration, brakes and more in a Jeep Cherokee.
These incidents have sparked continuing discussions inside and outside the trucking community. They are part of a growing concern over vulnerabilities in “internet of things” (IoT) devices. These are not only phones and computers, but also modern home appliances, vehicles and the like that open connections to the Internet.
The impending Dec. 18 electronic logging device mandate puts more focus on potential hacking in trucking. Most ELDs open up a connection to the cellular data network, whether directly or through paired smartphones or tablets. (The notable exception is the base version of the Continental VDO RoadLog.)
ELD makers partially downplay the threat. They say their devices aren’t set up to write to the engine’s electronic control module – only to receive and transmit data from it and that they have various security measures in place. Nevertheless, scanning for vulnerabilities in IoT devices has been on the rise in recent years as hackers look for ways to turn problems into opportunity. Much more hacking is expected, possibly via ELDs.
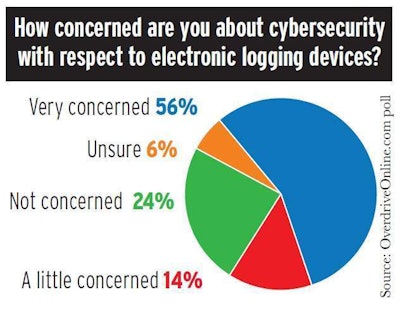
ELD system designers also increasingly are taking security into account. “I think we’re at an inflection point in the industry,” says Sharon Reynolds, Omnitracs’ chief information security officer. Guarding against vulnerabilities should be even more of a chief concern for everyone in the industry, Reynolds says.
Owner-operator Chris Guenther knows what it feels like to lose some control over a truck’s electronics, as was noted in a similar report earlier this year here. Last summer, he was fresh out of the shop with his 2012 Kenworth T700 powered by a Cummins ISX. Going across Southern Ohio toward Erie, Pennsylvania, his Omnitracs MCP50 onboard unit began switching log statuses erratically and flickering on and off.
“My dashboard started popping all kinds of engine and re-gen codes,” Guenther says. “The truck then de-rated” slightly, but he was many miles away from a good place to get service or even pull off.
Guenther called the shop that had just worked on the truck and was referred to Omnitracs, where a tech-support representative recommended a forced reboot. “He told me, ‘It’s going to shut down and reboot five times in a row,’ ” with about 10 seconds between each reboot, he says. “I’m still going 60 mph trying to keep it going. So he does that, and when the MCP50 shut down, so did my engine. It did that five times.”
The representative, when told what was happening, said, “This doesn’t normally happen.”
“We don’t have another documented case like this,” says Scott Hildebrandt, Omnitracs’ vice president of support and customer experience, who reviewed Guenther’s experience. “We definitely see the unit reset and see the unit come back up, but we can’t prove or disprove anything that happened out there.”
Guenther says moisture could have caused his problems. “I’ve got an issue with water getting into my harness plug [on occasion] that kicks off a slew of different codes.”
Asked about Guenther’s case, Cory Hunt of Pivot Technology Resources, a remanufacturer and reseller of used ELDs, says he’s heard of similar cases. “When you’re tying into the data connectors and some of the wiring in these trucks, they’re all integrated into the functionality of the trucks themselves,” Hunt says. “I’ve seen it where the onboard unit won’t even let the truck shut off,” even with the ignition key removed. In such cases, the truck won’t power down without powering down the onboard communications device.
“I’ve seen some really crazy things over the last 17 years,” he says. “They’re funny to hear” sometimes, but scary if you’re the victim. While such instances are rare, they suggest that ensuring the integrity of your truck’s electronic system will be doubly important when plugging in any IoT device, including an ELD, Hunt says.
A company such as Omnitracs has a large security staff, Reynolds says – likewise the capability of over-the-air software updates, enabling quick protection against malware and hackers. “When you select the IoT device, make sure it was engineered with security in mind,” she says.
ELD suppliers say the probability of hacking into electronic logs either the current automatic onboard recording device standard (49 Code of Federal Regulations 395.15) or the new ELD standard (49 CFR 395.16) to access the controller area network (CAN) bus of vehicles is virtually impossible, as ELDs are provisioned only to read data.
“We don’t give (our application) rights to be able to write or make requests,” says Marco Encinas, marketing and product manager for Teletrac Navman, which offers the Director ELD. “All we do is read. There is no protocol in the system that allows us to engage, change code for or manipulate the ECM computer on the vehicle.”
Encinas says he’s seen glitches like those experienced by Guenther. “The dashboard starts lighting up” and indicating fault codes and the like, he says, but things return to normal when the onboard unit is unplugged. He says it’s a result of an “incompatibility between the protocol we’re reading and the protocol the vehicle is broadcasting.”
In the case of a newer vehicle, it could be the vehicle manufacturer “changed a pin on the plug” so that it’s function was also changed.
As an extra layer of precaution, PeopleNet has embedded chips in its ELD devices to verify a secure connection.
“Our latest devices will all ship with an encryption chip built in to authenticate the device to the cloud in addition to standard authentication of the driver’s credentials upon login,” says Eric Witty, the company’s vice president of product. “That way, we have assurance that both the device and the person are authenticated in our system.”
Through PeopleNet’s partnerships with truck makers, “we continue to undergo security audits and improvements to our software and hardware solutions to ensure we minimize any risk of these telemetry devices being exploited to access the vehicle,” Witty adds.
Encinas says that perhaps the biggest risk for an owner-operator may be the physical connection to the ECM itself. While a sophisticated hacker “could find a way to generate that protocol to write into a vehicle’s ECM, to go through our device would be extremely hard. If someone wanted to do it, most likely they’d unplug it and insert their own hardware directly.”
Regarding his incident, Guenther says, his customer support representative speculated an over-the-air update didn’t go through to his unit because of a solar storm happening at the time the update was transmitting. Missing the update possibly contributed to the problems.
Guenther says his unit ran fine for months following the incident, but questions still bothered him. If the Omnitracs representative could control the unit from afar, who else could do the same? He takes that further, noting that if fault codes are being thrown by the ECM, “What’s to say that’s not somebody hacking the system and telling it that something’s wrong? It scares the hell out of me — a huge Pandora’s Box.”
To date, there’s no public evidence that a truck has been hacked maliciously. The University of Michigan researchers, plugged into the truck, were far from simulating a more difficult remote hack through an ELD or other access point.
But, says Omnitracs’ Reynolds, Guenther is asking the right questions. All industry parties need to cooperate to “continue to mitigate those risks,” she says. “We all have a hand in this game.” – Aaron Huff contributed to this report.